Glossary

A
Accuracy
Accuracy
Accuracy is the cornerstone of identifying fraud. When detection measures aren't up to par, it's easy to miss signs of fraud. According to Anura client case studies, our systems register virtually zero false positives. That means that our defenses don't block real visitors, ensuring no loss of potential revenue from actual customers. Most of the competitors have false-positive numbers (some in the double digits), putting a significant damper on campaign effectiveness.
Our resources can find gaps the other guys can't – and that means we can make sure no stone goes unturned. When Anura says it's bad, it's bad.
Ad Blocker
Ad Blocker
Anura Script will detect and report if the visitor is using an ad blocker.
Ad Fraud
Ad Fraud
Ad fraud is the practice of viewing, clicking, converting, or generating false interactions with any web asset for the sole purpose of earning money directly or indirectly. These actions are solely profit-driven and have no ties to the actual content of the advertising. Fraud can involve bots, malware, humans, or a combination, depending on the end goals of the fraudsters. Get the Ad Fraud 101 eBook now!
Ad Fraud Calculator
Ad Fraud Calculator
Ad Hiding
Ad Hiding
Ad hiding is a strategy that involves hiding ads in some way on a website. In this scenario, visitor traffic is legitimate, but the ads are never seen. There are a few techniques that fraudsters use to hide ads, including pixel stuffing and ad stacking.
Ad Injection
Ad Injection
Ad injection is a more nefarious pathway for fraud. This method uses malware to infect a website to override normal ad placement protocols. This opens a site up to unwanted advertising, which can be placed in spots that haven't been paid for or, worse, were purchased by legitimate advertisers. Most injected ads are irrelevant to the website in question or feature inappropriate content. Due to the malware required to achieve this strategy, ad injection poses a significant risk to the sites in use. This scam can affect companies of all sizes.
Ad Network
Ad Network
An advertising exchange that connects advertisers to potential new consumers by way of websites owned by publishers. The idea is that the ad network collects hundreds or thousands of publishers, aggregating all of their web properties into their network, and then allows advertisers to pay to have their ads shown across the network based on a variety of targeting criteria.
Ad Stacking
Ad Stacking
Ad stacking is a way to hide ads on a page for the sake of maximizing the number of impressions while saving website real estate. Using this strategy, ads are stacked on top of one another so that only the top ad is visible. While all of the ads register impressions when visitors visit the website in question, the visitor will only see one ad per stack. All of the other ads included in a stack will fail to perform as they can't be seen by visitors to the site. This technique implies that a site provides a large number of impressions, even though traffic is largely worthless.
Ad Tag Protect™
Ad Tag Protect™
AdTag
AdTag
An ad tag is a snippet of code that a publisher inserts into their webpage. This code fetches and displays an advertisement from an ad server. When a visitor lands on the publisher's webpage, the ad tag directs the request to an ad server, which then returns the appropriate advertisement for that specific visitor.
Advertiser
Advertiser
The company or brand paying for the offers that promote their product or service.
Advertising Arbitrage
Advertising Arbitrage
Advertising arbitrage is a strategy where marketers buy low-cost advertising space (e.g., via display ads, social media, or search engine traffic) and direct that traffic to higher-revenue generating channels, such as premium ad networks or affiliate offers. The goal is to earn more from ads or sales than what was spent on acquiring the traffic, capitalizing on the difference as profit. It requires careful management of traffic quality and cost-effectiveness to avoid losses.
Advertising Bot
Advertising Bot
Affiliate Hijacking
Affiliate Hijacking
Affiliate ID Swapping
Affiliate ID Swapping
Fraudsters replace the original affiliate ID with their own, hijacking the commission from the legitimate affiliate.
Affiliate Marketing
Affiliate Marketing
Affiliate Marketing is a type of performance-based marketing in which a business rewards one or more affiliates for each visitor or customer brought by the affiliate's own marketing efforts. This can be in the form of impressions, clicks, leads, or eCommerce. Download our Affiliate Marketing Fraud 101 eBook now!
Affiliate Marketing Fraud
Affiliate Marketing Fraud
Affiliate marketing is a marketing avenue in which businesses pay affiliates who can draw in new visitors or customers. Generally, the affiliate receives some sort of kickback for every new action generated, which can be in the form of impressions, clicks, leads, or eCommerce purchases. Affiliate marketing fraud aims to cheat merchants, buyers, or legitimate affiliates through the use of misleading or fraudulent activities to earn illegitimate commissions.
Aged Lead
Aged Lead
Anura Direct
Anura Direct
Anura’s flexible integration provides server-to-server communication to accommodate all environments. Anura Direct is designed to determine in milliseconds the most common types of fraud (General Invalid Traffic or GIVT) delivering real-time analysis in time-sensitive situations. Ideally used for pre-bid, post-ping, scraper bots, email, and more.
Anura Script
Anura Script
Anura Script, our preferred method of integration, collects hundreds of data points on each visitor to help identify the most advanced fraud techniques. Its quick and easy JavaScript integration is flexible for any environment. Anura’s ability to identify real customer activity vs. bots, malware, and human fraud allows you to make real-time marketing decisions that boost your ROI.
Anura's Core Values
Anura's Core Values
“Anura's Core Values are part of our DNA and make up our name A-N-U-R-A”
Authentic: We are REAL people providing a REAL solution to a REAL problem.
Never Satisfied: We innovate, develop, challenge, celebrate, and then we do it all again.
United: Our culture is open and diverse, yet we are a united team in accomplishing our mission.
Reliable: We rely on each other to encourage success, excel at our tasks, and provide support.
A Lot of Fun: We enjoy practical jokes, nicknames, and identifying fraud all while having fun.
Anura's Mission
Anura's Mission
Our mission is to increase our clients’ growth by improving marketing results through accurate and effective ad fraud mitigation. We work diligently with our clients to prevent fraudsters from accessing marketing dollars by innovating game-changing technologies.
Anura.io
Anura.io
Anura is an ad fraud solution with almost two decades of development experience driving its success. Our solution helps our clients find and mitigate some of the most complex types of fraud giving them increased campaign performance, enhanced ROI, and peace of mind from their online marketing campaigns.
API
API
Stands for Application Programming Interface. This is the protocol that a developer uses to access a company’s services programmatically.
API Library
API Library
The library that hosts API's, or Application Programming Interface. The library is a collection of code that developers need to build new projects.
Artificial Bot
Artificial Bot
Auto-Refresh
Auto-Refresh
When a website owner wants to increase the number of impressions they can sell, they can automatically refresh the page, part of the page, or just the ad unit itself to generate more impressions while the visitor is spending time on the site. For example, if a visitor spent an average of three minutes on a site, and if just one ad unit was updated every 10 seconds, this would translate to a sale of 18 ad units instead of just one.
It's important to note that the use of auto-refresh features isn't always ad fraud. In some cases, web visitors may utilize auto-refreshing add-ons to check for changing page content. This may be done when trying to purchase tickets to an in-demand show or looking for new posts on a forum.
B
Backlink Checker Bot
Backlink Checker Bot
This type of bot is an SEO specialist’s best friend. Backlink checkers crawl websites and search for inbound links to see where traffic originates. Using the bots’ findings, SEO specialists can make the necessary website and campaign changes to keep visitors coming. Get our Bots 101 eBook now!
Bad Result
Bad Result
Using Anura Script, we are 100% confident that this is not a real visitor. Our successful clients block or otherwise divert bad visitors to create the cleanest and most valuable traffic for themselves and their clients.
Banners
Banners
Banners are image-based rather than text-based ads that are used to promote a brand and/or to get visitors (traffic) to the advertiser’s website.
Bot
Bot
Short for “robot,” a bot is an automated software program built to carry out a specific task. Bots do jobs that most people would find too repetitive or time-consuming, like answering chat questions easily found on the FAQ page or updating numbers like stock prices at preset intervals.
Unethical programmers can re-tool bots for malicious purposes in a variety of ways; often designing malicious bots to serve malware, take over networks, steal information, plagiarize content, and steal marketing dollars from unsuspecting advertisers.
Bots usually mimic normal activity and can be hard for advertisers to detect. Bot fraud usually involves the use of bot farms or large collectives of bots that act in unison usually referred to as a botnet.
Bot Advertising
Bot Advertising
Bot Detection
Bot Detection
Bot detection is the process of identifying and blocking automated bot traffic to protect websites from fraud and other harmful activities. Effective bot detection solutions, like Anura's, analyze traffic patterns and session data both pre- and post-click, using techniques such as device fingerprinting and machine learning. This helps businesses prevent bot-driven fraud, including ad click fraud, account takeovers, and inventory hoarding, thereby preserving data accuracy, reducing financial losses, and securing user data.
Bot Detection Software
Bot Detection Software
Bot detection software is a tool designed to identify and flag automated bot traffic on websites and apps. Using techniques like machine learning, pattern recognition, and environmental analysis, it distinguishes between human users and bots. This software helps protect against fraud, maintain data accuracy, and secure digital assets by blocking bots from performing harmful activities such as click fraud, credential theft, or spamming.
Bot Fraud
Bot Fraud
Bot fraud refers to deceptive activities conducted by automated software (bots) to mimic legitimate human interactions online. Common forms include ad click fraud, where bots artificially inflate clicks or views on ads, and form spam, where bots fill out web forms with fake information. Bot fraud skews analytics, wastes advertising budgets, and poses security risks, as it often aims to exploit weaknesses for financial gain or data theft. Effective bot fraud prevention tools identify and block these bots to ensure accurate data and protect revenue.
Bot Prevention
Bot Prevention
Bot prevention involves actively blocking malicious bot activity to safeguard websites and digital assets from automated threats. This approach uses detection technologies to identify bot behaviors and stop them before they cause harm, such as click fraud, credential stuffing, or skewing analytics. Bot prevention tools combine real-time data analysis, machine learning, and rules-based filtering to distinguish between legitimate users and bots, ensuring accurate data and protecting revenue.
Bot Protection Software
Bot Protection Software
Bot protection software is designed to identify, prevent, and mitigate bot-based threats targeting websites, applications, and networks. It combines advanced detection techniques, such as environmental analysis, machine learning, and real-time monitoring, to distinguish between human users and malicious bots. This software safeguards against issues like ad fraud, credential stuffing, and data scraping, ensuring accurate analytics, secure user experiences, and reduced financial losses.
Bot Traffic
Bot Traffic
Bot traffic refers to non-human visitors—automated programs or scripts—that load webpages, click links, or fill out forms. Some bots are legitimate (like search engine crawlers), but in digital marketing, most are used to commit fraud.
Botnet
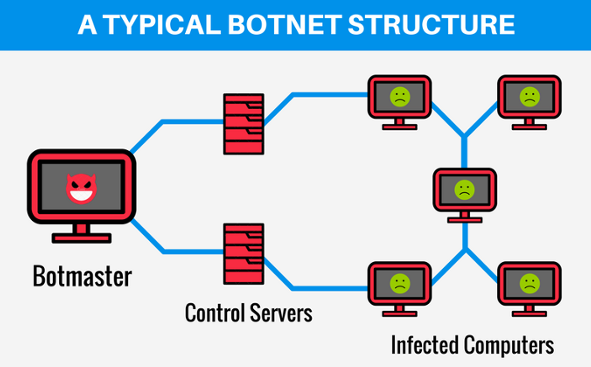
Botnet
As the name suggests, zombie bots turn computers into mindless drones, letting hackers control them remotely without visitors knowing their machine’s been compromised. A collection of zombie bots makes up a botnet. Here, affected computers work simultaneously to perform a certain task. Botnets are usually responsible for DDoS attacks.
Brand Safety
Brand Safety
The term used to protect the reputation of a brand from having its ads associated with questionable or inappropriate content. What makes it difficult is that each brand will have different tolerances for what they consider to be safe. For example, what Disney considers brand safe is different than what Victoria Secrets would consider safe.
C
Cache
Cache
Cache: Is a computer device, either hardware or software, that is designed to store data in a way to be able to serve it up faster when the data is requested again.
Callback Lead Scams
Callback Lead Scams
Fewer prospective customers fill out call-back forms than newsletter subscriptions and the like. As such, these are generally higher quality leads. That is unless they're fake. Fraudsters often fill out these forms with other people's information in order to receive compensation for doing so. The issue comes in when you call someone who didn't personally provide their consent, which may result in a TCPA-related lawsuit.
Campaign
Campaign
As it relates to the Anura Dashboard, is subset variable of "source," declared by you, to identify "campaign" traffic within Anura's dashboard interface. A campaign is the name used for a collection of ads that are running together to drive visitors to engagement, conversions, traffic, or revenue.
CAPTCHA
CAPTCHA
CAPTCHA is an acronym for “Completely Automated Public Turing test to tell Computers and Humans Apart”. It is a system designed to identify humans versus automated software. This was initially used to block bots from entering certain areas of websites. As bots became more sophisticated, CAPTCHA software had to evolve, however, it cannot stop human fraud.
Carding
Carding
Carding is a type of cybercrime in ecommerce where fraudsters use stolen credit card details and automated bots to test which cards are valid. This process, also called credit card stuffing, falls under automated transaction abuse.
The stolen data used in carding includes the cardholder’s name, credit card number, expiration date, CVV code, ZIP code, and birthday. Once verified, the valid card details are used for purchases or resold on the dark web.
Chatbot
Chatbot
Chatbots are programs designed to communicate with people using artificial intelligence. Chatbots specialize in answering specific questions or doing certain tasks. For instance, your bank account may have a 24/7 chatbot that will notify you when any suspicious activity happens within your account. Companies can deploy simple chatbots on platforms like Slack and Facebook Messenger or a more advanced chatbot like Amazon’s Alexa.
Chatbots can be both good and bad. Bad chatbots emulate human interaction by engaging in conversation. These bots attempt to acquire personal information and often reside on service websites like dating sites, messaging apps, or chat rooms.
Civil Investigative Demand (CID)
Civil Investigative Demand (CID)
A Civil Investigative Demand (CID) is an administrative subpoena that allows federal government agencies to request extraordinary amounts of information from private entities without going through any formal court procedures. - Wikipedia
Click Bait
Click Bait
A sneaky advertisement that captures your attention and entices you to click on their link (aka the bait). Once you click on the ad you only see a small piece of content. To see more, you need to click next to move to each page to see additional content while getting exposed to a large number of ads. An example would be “Click here to see the 10 ugliest dogs”. When you click, they show you one image of a dog with a bunch of ads surrounding the content and a button to see the next picture.
Click Bot
Click Bot
Advertisers are all too familiar with click bots. These bots intentionally visit sites and click on ads with the goal of warping ad campaign data and burning through an advertiser’s budget. For advertisers who pay on a CPC basis, click bots can be devastating.
Click Bot Platform
Click Bot Platform
A click bot platform is a larger system or service that manages widespread click fraud operations. Instead of one bot generating clicks, these platforms coordinate thousands of automated bots simultaneously. By using rotating IP addresses and automation tools, click bot platforms can make fraudulent traffic appear legitimate, making it more difficult for advertisers to detect wasted spend.
Click Bot Software
Click Bot Software
Click bot software is a program designed to simulate human interactions by clicking on ads, links, or websites. Fraudsters use this software to artificially inflate traffic numbers, drain ad budgets, and mislead advertisers into thinking campaigns are performing well. Unlike real visitors, click bots never convert into paying customers. Every fake click wastes marketing spend while delivering no business value.
Click Farm
Click Farm
A click farm is a fraud organization that leverages large groups of cheap workers to manually click on paid ads online. Like their bot counterparts, human click farms wreak havoc on the digital advertising ecosystem. Click farms have people clicking on ads with no intention of converting. They just visit sites and rack up worthless impressions.
Click farms may leverage form bots to fill out forms with bogus information, generating false leads, and creating a real nightmare for online advertisers who need reliable leads.
Click Flooding
Click Flooding
Click Fraud
Click Fraud
Click fraud is when bots, malware, or a human fraudster intentionally generates a bogus click on paid ads and links to steal money from pay-per-click advertisers or to exhaust an advertisers’ campaign budget.
Click Injection
Click Injection
Click Spamming
Click Spamming
Fraudsters use the concept of a Denial of Service (DOS) to attack networks in order to steal money from their advertisers. With a click spamming attack, the fraudster floods the network with enough clicks to attempt to overwhelm the networks billing software and trick it into paying the fraudsters.
Click Tag
Click Tag
A click tag is used within an advertisement to track and report clicks. Whereas an ad tag calls the ad content to be displayed, a click tag monitors when an ad is clicked, helping advertisers measure engagement.
Click-Through Rate
Click-Through Rate
Clickjacking
Clickjacking
Client Chargeback
Client Chargeback
In a digital marketing context, a client chargeback occurs when a client perceives that the services, they paid for were not adequately provided. This perception might stem from various issues such as suboptimal ad placement, failure to deliver ads as promised, or poor quality, often associated with fraudulent activities affecting their account.
Competitor Fraud
Competitor Fraud
Comprehensive Analytics
Comprehensive Analytics
Analytics are at the crux of identifying fraud, providing a way to capture concerning trends that highlight problematic activity. Anura's extensive dashboard allows visitors to customize reporting with the ability to drill down multiple levels, highlighting areas of primary concern. This tool allows you to pinpoint exactly where the fraud is coming from in order to block fraud with a few simple clicks.
Consistent Click Patterns
Consistent Click Patterns
Content Arbitrage
Content Arbitrage
Content Arbitrage is a digital strategy where publishers generate visitors to rich content pages and earn money from high-valued ads displayed on those pages. This approach focuses on creating or curating content that attracts viewers, and then monetizing that traffic through advertising networks, aiming to profit by generating impressions and clicks to those ads.
Content Delivery Network (CDN)
Content Delivery Network (CDN)
Content Delivery Network is a network that takes content from your server and caches it in high-speed servers around the globe helping to serve up content faster to people regardless of their location.
Content Marketing
Content Marketing
Content marketing is the process of planning, creating, distributing, sharing, and publishing content to reach your target audience. It can boost factors like brand awareness, sales, reach, interactions, and loyalty. (HubSpot)
Contextual
Contextual
An ad unit that is targeted to the content of the website. A script will "read" the page the ad is going to show on, interpret what the page is about, and then fetch an ad that is related to the content. A popular example of a contextual ad system is: Google Ad Sense.
Contextual Advertising
Contextual Advertising
Contextual advertising is a digital targeting strategy that delivers ads based on the content of the webpage a user is viewing. Instead of relying on cookies or personal data, contextual advertising matches ads to relevant topics, keywords, or themes on a page, ensuring users see ads that make sense in the moment.
Conversion Rate Optimization or CRO
Conversion Rate Optimization or CRO
Conversion Rate Optimization is a process aimed at increasing the percentage of visitors to a website who take the desired action, such as making a purchase, filling out a form, or engaging with content. It's not just about driving traffic to your site but ensuring that traffic is qualified and has a high propensity to convert.
Cookie
Cookie
A cookie is a text file within the visitor’s browser that a website can read and write small pieces of data to and from. Designed to provide a way for a visitor’s data to be remembered, Cookies store all types of stateful information between the visitor and the website, like browser or shopping history, login credentials, and other types of data.
Cookie Stuffing
Cookie Stuffing
Cookie stuffing is a sub-area of affiliate marketing fraud. Cookies are a big part of tracking web traffic and activities, but cookie stuffing uses this tool illegitimately to tag visitors. Fraudsters who cookie stuff, tag web visitors with cookies from unrelated websites that they did not visit without permission. These stuffed cookies affect how the activities of visitors are seen online. If, for example, an affiliate marketer directs a customer to make a purchase, the cookies will link back to the fraudster, who will receive credit for the sale.
Copyright Bot
Copyright Bot
Online copyright infringement is rampant, especially with so much data being shared every day. To combat plagiarism and theft, copyright bots scour the web for stolen content, such as music and video clips. Sites like YouTube use copyright bots to flag and disable uploaded content that could be in violation of copyright laws.
Counter Bot
Counter Bot
CPA (Cost Per Action)
CPA (Cost Per Action)
The billing method the advertiser is charged each time a visitor completes a predetermined action such as completing a purchase, filling out a form, or downloading an app. CPA is sometimes referred to as "Cost Per Acquisition".
CPC (Cost Per Click)
CPC (Cost Per Click)
The billing method the advertiser is charged each time their ad is clicked. It is also known as pay per click (PPC).
CPL (Cost Per Lead)
CPL (Cost Per Lead)
The billing method the advertiser is charged each time a visitor successfully completes a lead form.
CPM (Cost Per Mille)
CPM (Cost Per Mille)
The billing method the advertiser is charged for every one thousand times their ad is displayed. It is typically referred to as "Cost Per Thousand", however, CPM actually stands for “Cost Per Mille”, Mille is Latin for one thousand.
Cross-promotion
Cross-promotion
When you partner with Anura, we mention all companies in our marketing campaigns when they integrate us onto their platform. In turn, they promote us, which creates a mutual promotion with dual-brand exposure.
CSS
CSS
CSS stands for Cascading Style Sheets. It is used to keep a common look and feel of your website including fonts, colors, layouts, and more while making it easier to make site-wide changes within a single document.
CTV (Connected TV)
CTV (Connected TV)
CTV stands for “connected TV” and is any television set used to stream video over the internet. These are most often videos that are streamed via apps that are downloaded. Devices that are classified as CTV devices are Smart TV – a TV with a built-in internet connection and media platform. (Wikipedia)
CTV Fraud
CTV Fraud
D
Data Center
Data Center
Anura scrutinizes a user's device and system-level identity for indicators of server-based criteria such as hardware, geo-location data, IP address and other factors commonly associated with data centers. By doing so, we can determine if a visitor originated from an established data center. If identified, Anura promptly flags these non-human visitors as fraudulent, providing clients with definitive assessments of visitor quality.
Data Center Traffic
Data Center Traffic
Data Integrity
Data Integrity
Anura monitors the consistency of visitor data by reviewing both the request and response data. This comprehensive approach guarantees that data integrity is ensured throughout the entire session. Any deviation from this standard is considered fraudulent activity and is promptly identified by Anura's fraud systems. The identification of such inconsistencies triggers the corresponding rule(s) within Anura's Data Integrity rule set, which helps to ensure the accuracy and reliability of visitor data quality assessments. Clients can rest assured that Anura's commitment to data integrity is unwavering and that the data analysis process is designed to provide them with the highest level of assurance possible.
DDoS Attack (Distributed Denial-of-Service Attack)
DDoS Attack (Distributed Denial-of-Service Attack)
Dedicated Support
Dedicated Support
When you have questions, Anura has answers. Live phone support is available Monday to Friday, from 8 AM to 5 PM at our headquarters in Delaware. Anura's software and technology experts are highly experienced in ad fraud detection, ensuring accurate and comprehensive information whenever clients need assistance.
Demand Side Platform (DSP)
Demand Side Platform (DSP)
Demand Side Platform, aka DSP, is a platform that advertisers use to buy advertising, typically on an impression basis.
Device Fingerprinting
Device Fingerprinting
Device fingerprinting is a process that identifies a device based on its unique configurations and settings. It uses information like the device type, operating system, browser settings, installed fonts, and even screen resolution. The sum of this information creates a "fingerprint" that can be used to recognize, track, or block a particular device.
Device Spoofing (UA Spoofing)
Device Spoofing (UA Spoofing)
In order to hide fraudulent traffic coming from the same device, fraudsters employ technology that will make their one device look like many other devices. This is also referred to as User-Agent Spoofing.
Digital Advertising
Digital Advertising
Digital advertising, also known as digital marketing, Internet advertising, online advertising, or web advertising, is a form of marketing and advertising which uses the Internet to deliver promotional marketing messages to consumers. The typical Way to Purchase Programmatic Ads is by DSP/SSP.
Digital Arbitrage
Digital Arbitrage
Digital arbitrage involves exploiting price differences for goods or services in different markets, often in the digital space. It typically refers to purchasing digital products, services, or traffic at lower prices and selling or monetizing them at a higher rate. In digital marketing, this can mean acquiring traffic cheaply through one channel and monetizing it via higher-paying ads or affiliate commissions, leveraging the margin for profit.
Digital Doppelgängers
Digital Doppelgängers
A bot that can mimic human behavior. With sophisticated algorithms, they can simulate mouse movements, keystrokes, and even browsing patterns. Secondly, they can operate at a scale that is impossible for humans. This means they can generate hundreds of clicks or form submissions in a matter of seconds.
Digital Marketing
Digital Marketing
Digital marketing is marketing that makes use of electronic devices such as computers, tablets, smartphones, cellphones, digital billboards, and game consoles to engage with consumers and other business partners.
Digital Marketing Arbitrage
Digital Marketing Arbitrage
Digital marketing arbitrage refers to the practice of acquiring traffic at a lower cost through channels like search engines, then monetizing that traffic through higher-paying ads, such as display or affiliate ads. The goal is to profit from the difference between the low cost of acquiring traffic and the revenue generated from advertising. This strategy can be risky without proper safeguards, potentially leading to penalties like account suspensions or clawbacks.
Direct Results
Direct Results
Anura Direct is designed to be used with clients who do not have the ability to place our JavaScript code on their web assets. It is best for server-to-server communication or when there is limited visitor information. Anura Direct delivers real-time analysis in time-sensitive situations, typically used for click analysis, pre-bid and programmatic campaigns.
Display Advertising
Display Advertising
Digital display advertising is graphic advertising on Internet websites, apps, or social media through banners or other advertising formats made of text, images, flash, video, and audio. The main purpose of display advertising is to deliver general advertisements and brand messages to site visitors. (Wikipedia)
Display Fraud
Display Fraud
Sometimes referred to as impression fraud or viewability fraud, display fraud is when an ad is not viewable to the human eye, but impressions are still counted. The most well-known fraudulent methods for this type of fraud are pixel stuffing and ad stacking. Fraud can also occur within mobile apps and on fake sites created by fraudsters. Due to impression fraud, advertisers are paying for exposure that never happened.
Domain
Domain
A domain name is an easy-to-read website address. It's what you type into the address bar on an Internet browser to view a specific website.
Domain Spoofing

Domain Spoofing
Domain spoofing is the act of driving fraudulent traffic to an illegitimate domain and making it appear as if that traffic comes from a trusted domain. Many advertisers build lists of trusted domains. When the fraudster spoofs a domain on that list, their traffic will be accepted. Another way is to use a "look-a-like" domain (aka URL substitution) to trick a visitor into visiting their site or accepting their traffic because their name looks like a trusted domain.
Drop
Drop
A Drop occurs when Anura Script does not correctly receive the required data to properly analyze the visitor. This may occur for a number of reasons such as a slow Internet connection or device, an integration issue, or intentional blocking or altering of our data package to avoid screening.
Dummy Websites
Dummy Websites
Some scam websites may appear legitimate at first glance but have little value in terms of content or products offered.
Duplicate Ad Requests
Duplicate Ad Requests
If an ad request is unintentionally sent multiple times for a single ad impression, it may be considered GIVT.
E
eCommerce
eCommerce
Also known as electronic commerce: the online process of conducting business activities such as buying, selling, and exchanging goods, services, funds, or data. It enables individuals and businesses to engage in digital trade and commerce through online platforms and services, eliminating physical limitations.
eCommerce Chargeback
eCommerce Chargeback
eCommerce Chargeback refers to a situation where a customer disputes a transaction made online, typically for reasons such as unauthorized use of their credit card, not receiving the goods or services as described, or any other issues related to online transactions. The credit card company will then reverse the charge, taking the money back from the merchant and returning it to the customer.
eCommerce Fraud
eCommerce Fraud
eCommerce, or online shopping, is predicated on conversions. When ads don't convert, placement becomes a question. In order to perpetuate eCommerce fraud, some particularly savvy fraudsters will use stolen credit cards to make transactions, creating a false conversion rate that warrants ongoing ad fraud.
eCommerce Fraud Prevention
eCommerce Fraud Prevention
Ecommerce fraud prevention helps protect your online store by blocking bad actors in real-time, preventing costly chargebacks, reducing product shrink, and safeguarding your merchant account from high fees or loss. This proactive approach saves time and money by stopping fraud before it affects your business.
eCommerce Fraud Prevention Tools
eCommerce Fraud Prevention Tools
Ecommerce fraud prevention tools are solutions designed to protect online businesses from fraudulent activities. These tools use advanced technologies like machine learning, IP tracking, and environmental analytics to identify and block fraud attempts in real time. Key features include detecting stolen credit card use, preventing account takeovers, reducing chargebacks, and stopping product shrink due to fraudulent orders. By implementing these tools, ecommerce businesses can secure transactions, protect revenue, and build customer trust.
eCommerce Fraud Protection
eCommerce Fraud Protection
Ecommerce fraud protection safeguards your online store by blocking fraudulent actors in real-time, preventing costly chargebacks, reducing product shrink, and protecting your merchant account. With Anura, you can secure transactions, maintain customer trust, and protect your business’s bottom line.
eCommerce Fraud Software
eCommerce Fraud Software
Ecommerce fraud software is a specialized tool or platform designed to detect, prevent, and manage fraudulent activities on online stores. It uses advanced algorithms, machine learning, and real-time data analysis to identify suspicious transactions, such as stolen credit cards, account takeovers, and high-risk orders. The software helps businesses reduce chargebacks, protect merchant accounts, and prevent financial losses by blocking fraud before it impacts the business. It ensures secure online transactions, improves operational efficiency, and safeguards both the business and its customers.
EEAT
EEAT
EEAT stands for experience, expertise, authoritativeness, and trustworthiness. Experience refers to the hands-on knowledge or skill that content creators possess in their respective fields. Expertise is about having formal and comprehensive knowledge in a specific area. Content that showcases a high level of expertise, particularly in specialized fields like medicine or finance, is deemed more credible. Authoritativeness hinges on the reputation of the website or content creator. A site or individual recognized as a leading authority in their niche garners higher trust and respect. Trustworthiness encompasses the accuracy, honesty, and reliability of the content, its creators, and the hosting website. Factors like website security, clear privacy policies, and transparent authorship are crucial in establishing trustworthiness.
Eliminate Bots
Eliminate Bots
This refers to using detection and prevention techniques to completely block malicious bots from accessing or interacting with a digital platform. This involves identifying bot behaviors and stopping them at various points, from login attempts to clicks, to protect against fraud, maintain accurate data, and secure user interactions.
Email Marketing
Email Marketing
Email marketing is sending an email to a list of potential clients to promote your product or service and to build loyalty, trust, or brand awareness. Email marketing can be done to either cold lists or the current customer databases.
Enumeration Fraud
Enumeration Fraud
Enumeration fraud is a type of cyberattack where fraudsters systematically test combinations of usernames, passwords, credit card numbers, or other personal data to gain unauthorized access or validate stolen credentials. Often by using bots or automated scripts, these attacks can target login pages, checkout forms, or account recovery systems. This type of fraud can lead to account takeovers, fraudulent purchases, and data breaches.
F
Fake App Installations
Fake App Installations
Fake Leads
Fake Leads
Fake leads refer to fraudulent or non-genuine prospects that mislead businesses into thinking they are valuable leads. These can include bots, bogus contact information, or individuals who have no intention of converting into customers. Fake leads waste marketing resources, distort performance metrics, and hinder effective lead generation efforts. Identifying and filtering out fake leads is essential for optimizing marketing strategies and ensuring high-quality, actionable leads.
Fake Post-View Conversions
Fake Post-View Conversions
Fake Reviews
Fake Reviews
Affiliates may post fake reviews or ratings on websites and social media in order to mislead customers into buying a product or service.
Fake Traffic
Fake Traffic
Some affiliates will generate fake traffic in order to boost their commissions. This could include using automated bots or paying people to click on links.
False Advertising
False Advertising
Many scammers use fake or misleading ads to lure in unsuspecting customers.
False Positive
False Positive
In terms of ad fraud, false positives are when a real visitor is incorrectly identified as a fraudulent visitor. Due to the decades of research that Anura has, we claim that we have “no false positives”.
Feed Fetcher Bot
Feed Fetcher Bot
These bots work around the clock to bring you real-time data like updates on the news, currency exchange, and weather. They also specialize in collecting and sending information between websites and mobile or web applications.
File-Sharing Bot
File-Sharing Bot
These bots act as malware delivery men. They post malware-infected files on peer-to-peer file-sharing services, such as Dropbox. Thinking the file is legitimate, the visitor downloads it, but they just installed malware onto their computer.
Forced Redirects
Forced Redirects
Users are redirected to unrelated pages without their consent, inflating page views, and misleading advertisers about the source of the traffic.
Form Bot
Form Bot
Bad bots can fill out forms with the aim to access restricted content and make this content publicly available. This, in turn, may decrease the income generated through brands relying on premium content or subscription models.
Fraud Leads
Fraud Leads
Fraud leads are illegitimate contacts or prospects generated with the intent to deceive businesses into thinking they are real potential customers. Often created by bots, fake users, or malicious sources, fraud leads skew performance metrics, waste marketing resources, and harm lead generation efforts by diverting focus from genuine, actionable leads.
Fraud Prevention
Fraud Prevention
Fraud Rates
Fraud Rates
Fraud Rates represent the percentage of fraud across your instances, sources, and campaigns.
Fraud Trends
Fraud Trends
Keep track of the changes in Fraud Rate over time. This metric can be used to judge the effectiveness of your fraud mitigation strategy.
Fraudulent Leads
Fraudulent Leads
Fraudulent leads are fake or misleading contacts that appear as genuine prospects but are actually generated by bots, click farms, or individuals with no real intent to engage or convert. These leads distort marketing data, waste resources, and reduce the effectiveness of lead generation efforts. Identifying and filtering out fraudulent leads helps businesses focus on quality prospects and improves overall marketing ROI.
G
Game Bot
Game Bot
GDPR (General Data Protection Regulation)
GDPR (General Data Protection Regulation)
GDPR regulates the usage and collection of personal data, offering “user data protection” for European Union citizens . This protection extends to wherever a citizen travels, making it a global consumer privacy policy. To be eligible for protection, data must belong to a living identifiable person. A “living identifiable person” is defined as having a name, photo, medical information, and email address, plus a digital footprint.
General Invalid Traffic
General Invalid Traffic
General Invalid Traffic or GIVT refers to bots, crawlers, spiders, or any of the kind of non-human traffic typically routed from a data center IP address. GIVT can also apply to activity-based filtration or browsers that pre-render pages. Most of the time, GIVT is easy to identify and exclude from results.
Geotargeting Fraud
Geotargeting Fraud
Geotargeting fraud occurs when an advertiser targets specific geolocation. In this form of fraud, a fraudster sends ads from a different location, masking it to look like the location the advertiser targeted.
GIVT
GIVT
An acronym for General Invalid Traffic, referring to non-human traffic such as bots or crawlers; click here for the full definition.
Good Result
Good Result
Using Anura Script, the visitor passed all of our tests and is considered good. We feel this is a real person, with real conversion value.
Google Ads (AdWords)
Google Ads (AdWords)
Google Ads is an online advertising platform developed by Google, where advertisers bid to display brief advertisements, service offerings, product listings, or videos to web visitors. It can place ads both in the results of search engines like Google Search and on non-search websites, mobile apps, and videos. (Wikipedia)
Google AdSense
Google AdSense
Google AdSense is a program run by Google that allows publishers in the Google Network of content sites to serve automatic text, image, video, or interactive media advertisements, that are targeted to site content and audience. These advertisements are administered, sorted, and maintained by Google, and they can generate revenue on either a per-click or per-impression basis.
Website owners can enroll in this program to enable text, image, and, more recently, video advertisements on their websites. These advertisements are administered by Google and generate revenue on a per-click or per-impression basis. Google uses its technology to serve advertisements based on website content, the user's geographical location, and other factors. Those wanting to advertise with Google's targeted advertisement system may enroll through Google Ads.
AdSense is a way for website owners to make money by displaying Google ads on their websites. These ads are usually tailored to reflect the content of the web page they appear on or are based on the specific interests of the visitor to that page, which Google determines based on the visitor's browsing history.
H
Hacktivist
Hacktivist
Hidden Ads
Hidden Ads
Ads are loaded in areas users can't see, such as behind other content or in 1x1 pixels, so they're never actually viewed but still generate ad impressions.
Honeypot Technique
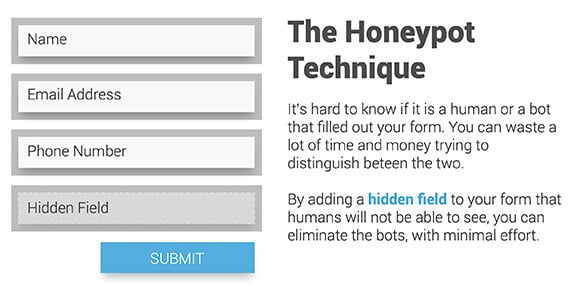
Honeypot Technique
Designed to capture bots without human visitors noticing, honeypots are a hidden form field that humans can’t see but bots can. They’ll immediately complete the form, letting the website owner know the visitor is actually a bot.
The only complication with this method is that humans using screen reader software will see the form and likely fail the test. You could label the field explaining its use, so real visitors know to leave it blank.
How to Stop Bots
How to Stop Bots
This involves using security measures to prevent automated bot traffic from interacting with your website. Common strategies include deploying CAPTCHAs, implementing bot detection software, and using environmental analysis to identify non-human activity. These tools filter out bots, protecting against spam, fraud, and data manipulation.
HTML
HTML
HTML stands for HyperText Markup Language. It is the basic scripting language of a website that instructs a web browser on how to display the website’s information. Within HTML, you can add other languages such as JavaScript and CSS to build more robust sites.
Human Fraud
Human Fraud
Human fraud is the hardest form of ad fraud to detect as it relies on a network of humans, instead of using bots or malware, to interact with ads and create false transactions. Because actual humans are interacting with the ads, there are no obvious signs that can differentiate normal traffic from human fraud.
Human Fraud Farm
Human Fraud Farm
I
Impersonator Bot
Impersonator Bot
As their name suggests, impersonator bots disguise themselves as humans and are so advanced as they sometimes go undetected. They mimic human behavior online, filling out forms and click-through sites. As bots become more sophisticated, security mechanisms like CAPTCHA are becoming easier for bots to crack.
Impression
Impression
Impressions can be in the form of display ads, video ads, or banners. Impressions are digital advertisements displayed on someone's screen. Sold in Cost per Thousand or CPM. An impression is counted every time it is displayed on someone’s web asset.
Impression Bot
Impression Bot
Fraudsters create decoy web pages full of both print and video ads. These bots continually load and reload these pages to create impressions, taking views away from legitimate websites, and decreasing their viewability stats.
Impression Fraud
Impression Fraud
(aka viewability fraud or display fraud) is when an ad is not viewable to the human eye, but impressions are still counted. The most well-known fraudulent methods for this type of fraud are pixel stuffing and ad stacking. Fraud can also occur within mobile apps and on fake sites created by fraudsters. Due to impression fraud, advertisers are paying for exposure that never happened.
Influencer Marketing Fraud
Influencer Marketing Fraud
In marketing terms, an influencer is someone who has a large following socially and can "influence" others to make specific buying decisions. Influencer marketing fraud occurs when an influencer is either using bots or other techniques to artificially inflate their engagement with the advertiser. Sometimes, the influencer isn't even a real person.
Instance
Instance
Invalid Proxy Traffic
Invalid Proxy Traffic
Invalid Traffic (IVT)
Invalid Traffic (IVT)
Invalid traffic, often known as IVT, refers to any form of web traffic that is derived from a non-human source. In some cases, this kind of traffic exists for a good reason, like search engine crawlers. However, most of the time, IVT is used to refer to fraudulent traffic.
IVT comes in a few different forms, including General Invalid Traffic, or GIVT. GIVT refers to bots, crawlers, spiders, or any of the kind of non-human traffic routed from a data center IP address. GIVT can also apply to activity-based filtration or browsers that pre-render pages. Most of the time, GIVT is easy to identify and exclude from results.
SIVT stands for Sophisticated Invalid Traffic. SIVT techniques are far more challenging to detect. This can include bots that closely mimic human traffic, hijacked devices, invalid proxy traffic, or cooking manipulation techniques, like stuffing.
IP Address
IP Address
An IP address, or Internet Protocol address, is a series of numbers that identifies any device on a network. It’s the “device number” people and computers use to connect to other devices on the internet. The IP address gives us basic information about the devices connecting to the internet such as geo-location, type of internet connection, service provider, etc.
IP Integrity
IP Integrity
An IP address is similar to a physical address and can be associated with fraudulent non-human activity and automated bots. This can lead to harmful activities targeting your assets. Anura validates each visitor's IP address for integrity using a combination of proprietary factors, as well as referencing historical data of the known malicious activity.
IP Masking or IP Spoofing
IP Masking or IP Spoofing
J
Jailbreaking
Jailbreaking
The term used when someone hacks an iOS device in order to gain higher levels of access, typically root access with admin privileges, to the device for the purpose of installing unauthorized software or features, that be the default, are prevented.
JavaScript
JavaScript
Also known as JS, JavaScript is a programming language used in web development that is a "client-side" language. This means the code is added in the HTML of a website and then executed on the website visitor’s machine. Anura uses JavaScript for the Anura Script integration method. This allows us to collect hundreds of data points on the visitor’s environment to help us determine whether a visitor is real or fake.
JQuery
JQuery
JQuery is a library of commonly used JavaScript functions designed to make it easier to build JavaScript functionality within your website.
JSON
JSON
JSON stands for JavaScript Object Notation. It is a lightweight format for passing dynamic data from one system to another. It has become a faster, more popular replacement to XML. JSON is the format that Anura uses to pass results to our clients.
K
L
Lead Flipping
Lead Flipping
Lead Generation
Lead Generation
Lead Generation is the business of advertising a product or service to consumers, whereby an interested consumer can fill out a form expressing interest and expecting more information in return. Lead generation campaigns are one of the top targets for ad fraud. See also: Lead Generation Fraud
Lead Generation Fraud
Lead Generation Fraud
Lead generation fraud is a subset of advertising fraud where fraudsters create fake leads for companies operating to collect money. This lead gen fraud can have a disastrous impact on a company’s ROI for their online and affiliate marketing campaigns.
In order to commit lead generation fraud, a fraudster will use a bot, malware, or humans to fill in the lead forms using stolen information, in order to bypass detection. This will create a myriad of issues for the advertiser.
Lead List Fraud
Lead List Fraud
Lead lists are contact lists purchased from a third party. They provide a quick, easy way to gain access to prospective customer information. However, not all lead lists are as they appear on the surface. Many are the product of fraudsters. If you purchase one of these, your company just spent money on a list of fake names and numbers — at the very least, on names and numbers that have no connection to your industry and have not provided their consent to be contacted. In most lines of business, lead lists are generally discouraged as a lead generation strategy, since many of the names on a lead list ultimately won't result in any actual conversions.
M
Macros
Macros
Variables containing dynamic data that are passed to Anura to be used within the analytics dashboard.
Made-For-Advertising Site or MFA
Made-For-Advertising Site or MFA
Malvertising
Malvertising
Malware Ad Fraud
Malware Ad Fraud
Malware is malicious software installed on an unsuspecting visitor's computer, either desktop or mobile, that is designed to perform specific tasks. For example, it can be used to steal personal information from the visitor or commit ad fraud. Malware ad fraud hijacks a unique device, mimicking a real visitor to perform tasks that steal advertising dollars by viewing or clicking on ads, watching videos, filling in forms, and other unsavory activities unbeknownst to the visitor.
Mismatched Referral Data
Mismatched Referral Data
Mismatched referral data typically refers to a situation where there is a discrepancy between the information provided by a referring source and the actual data pulled from the browser.
Mismatched User Agent
Mismatched User Agent
User-Agent strings can be manipulated or mismatched, leading to traffic that doesn't seem to align with typical browser behavior.
Mobile
Mobile
Anura will detect and report if the visitor is using a mobile device.
Mobile Ad Fraud
Mobile Fraud (Cellular Fraud)
Mobile Fraud (Cellular Fraud)
Mobile Fraud (Cellular Fraud) The FCC defines it as the unauthorized use, tampering, or manipulation of a cellular phone or service. Types of cellular fraud include SIM swapping, cloning, and subscriber fraud.
Mobile In-App Advertising
Mobile In-App Advertising
Mobile In-App advertising is where app developers get paid to serve ads on their apps. The app requests an ad from the network, and the network uses algorithms to identify and deliver the highest-paying ad to the visitor in real-time.
Mobile In-App Advertising Fraud
Mobile In-App Advertising Fraud
Mobile apps are a huge source of advertising. Many apps are fully ad-sponsored, providing a free platform for fun or function for visitors willing to put up with ads from time to time.
There are a few different ways in which fraudsters can use apps to defraud advertisers, but the primary method involves hiding ads to generate false impressions. Instead of making ads noticeable, like in video or banner form, ads are hidden in places visitors won't see, collecting impressions but without any visitor engagement.
Mobile Marketing
Mobile Marketing
Mobile marketing is a multi-channel online marketing technique focused at reaching a specific audience on their smartphones, feature phones, tablets, or any other related devices through websites, E-mail, SMS and MMS, social media, or mobile applications. (Wikipedia)
Mobile Web Advertising
Mobile Web Advertising
Mobile web advertising is where web developers get paid to serve ads to mobile web visitors.
Monitoring Bot
Monitoring Bot
Like digital doctors, monitoring bots make sure your website is running without any issues. These bots can detect where visitors are having trouble on your sites, such as areas of lag or unresponsiveness.
N
Native Advertising
Native Advertising
Native Advertising is designed to blend their ads with the look and feel of the site to make it harder for an individual to distinguish between an advertisement and regular content.
Non-identifiable
Non-identifiable
If Anura is unable to successfully identify a metric, it's value will be returned as (non-identifiable).
Non-Suspect
Non-Suspect
Based on the visitor data received, Anura did not find abnormalities consistent with invalid traffic. The visitor should be considered non-suspect.
O
O&O Websites (Owned & Operated)
O&O Websites (Owned & Operated)
Owned and operated means a business owns and controls a website. In lead generation, they drive traffic to their own sites to generate leads to give more control over how they process that lead. For example, they can sell the lead, they can call the lead and transfer the call, or they can sell a product or service directly to a client.
Online Advertising
Online Advertising
Online advertising, also known as online marketing, Internet advertising, digital advertising, or web advertising, is a form of marketing and advertising which uses the Internet to deliver promotional marketing messages to consumers. The typical Way to Purchase Programmatic Ads is by DSP/SSP.
Organic Search
Organic Search
OTT (Over-the-top)
OTT (Over-the-top)
An over-the-top media service is a media service offered directly to viewers via the Internet. OTT bypasses cable, broadcast, and satellite television platforms, the types of companies that traditionally act as controllers or distributors of such content. (Wikipedia)
P
Paid Traffic
Paid Traffic
Pay Per Call Fraud
Pay Per Call Fraud
Also called cost per call, pay per call is an agreed-upon rate paid by an advertiser for a call that meets the minimum call duration. In most cases, a duration of at least two minutes is required for a call to be considered a billable event, but this can vary based on advertiser needs and preferences. While more difficult to defraud an advertiser than web advertising, some fraudsters do target pay-per-call models. Calls are typically generated from landing pages that contain phone numbers but can also be bought and sold through call networks. Two techniques used to commit Pay Per Call Fraud are using an overseas call center or an avatar:
Pay Per Click
Pay Per Click
Pay per click is used to drive traffic to websites, in which an advertiser pays a publisher (typically a search engine, website owner, or a network of websites) when the ad is clicked.
Pay Per Click(PPC) Fraud
Pay Per Click(PPC) Fraud
Clicking on a link and then being taken to another website that pays the affiliate for each click.
Performance Based Marketing
Performance Based Marketing
A form of advertising when the buyer only pays the seller based on certain measurable results. Affiliate marketing and lead generation are 2 forms of performance-based marketing.
Phishing
Phishing
Some scammers may attempt to steal personal information and pass it off as a legitimate offer or service in order to get commission payments from advertisers. They may also use stolen credit cards to make purchases.
Ping Pick Post
Ping Pick Post
A new step has been added to the traditional Ping Post method. This step is called "Pick". The Ping Pick Post is a method of distributing leads in a sophisticated way that follows the guidelines established by the FCC's one-to-one consent. Comparison websites use it by means of auctions. The process begins by pinging potential buyers to request bids, ensuring they receive excellent deals, while companies get access to high-quality leads. Once a buyer picks an offer, their information is posted or shared with the selected companies for further interaction.
Ping Post
Ping Post
Ping Post is a method used in online lead generation and advertising, particularly in industries such as insurance and finance. It is a real-time transaction process that concerns the rapid exchange of information between lead generators, lead buyers, and intermediaries. This process involves two main stages: the "ping" and the "post."
Pixel Stuffing
Pixel Stuffing
Pixel stuffing is a fraudulent technique in which a standard ad is reduced in size and placed in a single pixel. The ad technically exists on the site and visitors trigger impressions. However, individual pixels aren't visible to the human eye, so viewers aren't able to view these ads. Any impressions generated using pixel stuffing are illegitimate, as visitors are unable to see any advertising in place. Because pixel-stuffed ads take up very little real estate, fraudsters can fill an entire site with pixel-stuffed ads to create the illusion of a significant number of impressions.
Playing Bot
Playing Bot
Post-Bid or Post-Click
Post-Bid or Post-Click
After you win the RTB (real-time bidding) auction and your ad shows, you can run your ad fraud solution to collect valuable targeting data and make real-time decisions on how to handle the visitor that is interacting with your web asset.
Potential Savings
Potential Savings
Estimated amount of money saved by implementing a trusted, real-time ad fraud solution.
Pre-Bid
Pre-Bid
This is the step in the RTB (real-time bidding) auction where you decide if you want to bid on the specific digital ad inventory. During this step, you can use an ad fraud solution to scan for GIVT (General Invalid Traffic) to help you make the decision.
Pre-Fetching
Pre-Fetching
Prevent Bots
Prevent Bots
This means implementing strategies and technologies to block automated bot traffic from interacting with digital platforms. This process leverages detection tools like environmental analysis, pattern recognition, and machine learning to identify non-human activity, filtering out harmful bots to protect against fraud, data manipulation, and security threats.
Programmatic Advertising
Programmatic Advertising
Programmatic advertising is digital marketing that uses software to decide when and where to place ads in front of a specific audience using a variety of rules and attributes. This style of buying is typically used for display and video, but can be used for a variety of other channels as well.
Programmatic Fraud
Programmatic Fraud
Programmatic fraud is a subset of ad fraud where nefarious individuals take advantage of programmatic advertising for financial gain. To employ this type of fraud, these individuals deploy bots, malware, and even human fraud, to falsify impressions and/or clicks to steal advertisers’ marketing budget.
Proxy
Proxy
Publisher
Publisher
A company or individual that owns a website where they publish a variety of content in order to build an audience. Publishers typically incorporate ad tags to monetize their audience by placing advertisements on their websites and those ads are usually managed by an ad network or supply-side platform (SSP).
Q
Quotes
Quotes
Quotes are a popular lead generation mechanism for businesses such as insurance companies that offer customized feedback for each potential client. This can be an effective way to entice prospective customers with an appealing deal, but it also opens the door for fraudsters. For companies giving insurance or financial-related quotes, lead generation fraud can compromise the integrity of databases and threaten companies' reputations as well as cause financial hardship.
R
Real-Time Bidding
Real-Time Bidding
Also known as RTB. This is the part of an ad exchange that lets buyers use their own criteria to determine if and how much they should bid for a specific ad unit. They can use data such as retargeting, interest-based targeting, ad fraud solution responses, etc.
Real-time Response
Real-time Response
A response that happens nearly instantaneously giving you enough time to make decisions before the fraudster has a chance to cause an issue.
reCAPTCHA
reCAPTCHA
This version of CAPTCHA is a service that is popular and offered by Google. It is designed to rate interactions with its test to attempt to determine the difference between humans and bots. Version 1 was the test that had a human check the box to prove they were not a bot. Version 2 became more complex with a fair percentage of humans failing to pick similar pictures. Version 3 requires no human interaction to do its test, but simply scores the visitor leaving the decision process up to the website owner.
Recycled Aged Lead
Recycled Aged Lead
Referrer
Referrer
The last URL that a browser loaded before landing on the current URL that it is on. This can be used to learn where a source of traffic came from before visiting the current web page. Originally, when it was incorporated into the HTTP specification, it was misspelled as 'referer' and has remained that way to this day.
Requests
Requests
Any time you query Anura to scan and analyze traffic. This can represent an impression, a click, a form fill, a credit card transaction, and many other forms of interactions with your web assets.
Residential Proxy
Residential Proxy
ROAS
ROAS
ROI (Return on Investment)
ROI (Return on Investment)
Return on investment, or ROI, refers to the returns yielded by investing in a particular cause or opportunity.
Rooting
Rooting
Rooting is the term used when someone hacks an Android device in order to gain root access with admin privileges for the purpose of installing unauthorized software or features, that by default, are prevented.
Rule Sets
Rule Sets
To make accurate judgments on visitor quality, Anura has built a continually growing list of rules and heuristics. To provide transparency as to why traffic is scored as bad or warning, we have categorized each of these rules/heuristics into one of seven different Rules Sets. Each of these Rule Sets has multiple rules/heuristics to ensure the accuracy of the Rule Set.
S
Sale Fraud
Sale Fraud
A type of fraud that occurs when someone uses stolen or unauthorized payment information to make a purchase. This can happen online, in person, or over the phone.
Savings Input (Non-Admin)
Savings Input (Non-Admin)
See how much you could be saving by using Anura’s certified ad fraud solution. To gain further insights, log in as an admin or contact support to update your information.
Schema
Schema
In the context of databases, a schema refers to the organization or structure of a database. It is a way to define objects in the database, like tables, columns, relationships, etc. A database schema is the blueprint that defines the database structure.
In the context of web-based markup languages, a schema is a set of rules that defines the structure and content of a document. The schema defines what elements and attributes can be used in a document, and the order and hierarchy.
Scraper Bot
Scraper Bot
Scraper bots "scrape" or steal high-quality, keyword-rich content from other websites and repurpose it on their own sites, skewing your website's search engine rankings. Stolen content can be hard to spot unless you make a point to search for it.
Script Result
Script Result
Anura Script uses JavaScript and is our most comprehensive method for collecting visitor data. It excels at identifying even the most sophisticated fraud in real-time. Ideally, Anura Script is used for conversions and post-click analysis.
SDK Spoofing
SDK Spoofing
A type of mobile ad fraud where fraudsters fake app install and in app events on actual devices.
Search & Social Protect™
Search & Social Protect™
Anura automatically hides ads from fraudsters before they have a chance to fraudulently click on them. Test the power of Anura, click here.
Search Arbitrage
Search Arbitrage
Search Arbitrage is a digital marketing strategy that involves buying traffic through different paid marketing channels and then earning revenue through higher-priced ads on the landing page.
Typically, this involves the use of pay-per-click (PPC) advertising platforms, such as Google AdWords, Yahoo, etc, where an advertiser may bid on specific keywords to drive traffic to a page that hosts ads from another network or direct offers. The arbitrageur's profit is the difference between what they pay for the incoming traffic and what they earn from the outgoing traffic. This practice requires a deep understanding of keyword valuation, ad placement optimization, and traffic conversion rates to be successful and profitable.
Search Arbitrage Fraud
Search Arbitrage Fraud
Search Engine Bot
Search Engine Bot
A crawler or spider is a bot that crawls web pages on behalf of search engines. They process and analyze the content of a web page to figure out its meaning and relevance. Depending on what they find, search engines can use that info to gauge a page’s reliability and organic SERP ranking.
Search Engine Marketing (SEM)
Search Engine Marketing (SEM)
SEM is a marketing channel that targets visitors by interest through the use of the search terms the visitor has typed in, in the search engine. These ads are text-based, paid placements and have a number of targeting criteria. This channel is also known as PPC (Pay Per Click) marketing.
Search Engine Optimization (SEO)
Search Engine Optimization (SEO)
SEO is the process of improving the understandability of the true content of a web page to a search engine’s algorithm to appear more relevant and gain higher rankings in the organic search results pages (also referred to as SERP)
Search Engine Optimization Fraud (Black Hat SEO)
Search Engine Optimization Fraud (Black Hat SEO)
Search Engine Optimization Fraud or Black Hat SEO is a practice against search engine guidelines, used to get sites ranking higher in the SERPs. These unethical (sometimes illegal) tactics don’t solve for searchers and often end in penalties from Google. Black-hat techniques include keyword stuffing (i.e. adding lots of words just so you appear relevant), cloaking—using artificial algorithms or scripts that mask where content came from when it was generated on other websites/blogs--and using private link networks which are groups designed specifically around exchanging links between members.
Search Engine Results Page (SERP)
Search Engine Results Page (SERP)
This is a page of results that a search engine returns in response to a visitor’s search request based on the search engine’s algorithm. This will contain a mix of paid and organic listings ordered based on a variety of metrics used by the search engine.
Search Feed Arbitrage
Search Feed Arbitrage
Search feed arbitrage is a tactic where marketers buy traffic from one search engine or platform at a low cost and redirect it to higher-paying search feeds or monetized search result pages. The aim is to profit from the margin between the traffic acquisition cost and the revenue generated from displaying ads on the landing page. This method requires optimization to ensure the traffic is relevant and aligns with ad network policies to avoid penalties.
Search Fraud
Search Fraud
Self-Dealing
Self-Dealing
When an affiliate uses the merchant's affiliate links for their purchases to earn a commission.
Single Sign-on (SSO)
Single Sign-on (SSO)
Single sign-on is an authentication scheme that allows a user to log in with a single ID and password to any of several related, yet independent, software systems. True single sign-on allows the user to log in once and access services without re-entering authentication factors. (Wikipedia)
SIVT
SIVT
An acronym that stands for Sophisticated Invalid Traffic. See the full definition here.
Social Media Fraud
Social Media Fraud
Social media fraud involves deceptive activities carried out on social networking platforms(Facebook, Instagram, LinkedIn, TikTok, Twitter, and YouTube) with the intention of making money indirectly. Fraudsters create fake profiles and interact with other profiles, ads, and leads in a manner that mimics genuine visitors, to avoid detection and account suspension. A quick search on Fiverr will show that you can buy 10,000 likes for your site for $5. Advertising on social networks allows fake influencers to comment, like, and influence consumers to trust a brand.
Social Media Marketing
Social Media Marketing
Social media has become a powerful internet marketing tool in recent years. Platforms like Facebook, Instagram, and YouTube provide space for dynamic two-way communication between brands or visitors alike with the ability to create content that isn't limited by pre-existing rules of engagement (therefore allowing anyone an equal opportunity). There are two types of social advertising - paid advertisement which seeks financing via money spent on ads; organic campaign where advertisers don’t invest any cash at all but rather use their own resources such as time into building relationships through likes/followers, etc., attracting new customers using these methods so they may tell others about what you offer afterward when asked: "where did u get ___?"
Social Network Bot
Social Network Bot
Ever wonder how certain posts appear in your social news feeds? Social networks like Facebook and Twitter rely on proprietary bots to run data through algorithms and serve posts based on visitor behavior.
Sophisticated Invalid Traffic
Sophisticated Invalid Traffic
SIVT stands for Sophisticated Invalid Traffic. SIVT techniques are far more challenging to detect. This can include advanced bots that closely mimic human traffic, hijacked devices, malware, invalid proxy traffic, cookie manipulation techniques, like cookie stuffing, or human fraud farms.
Source
Source
As it relates to the Anura Dashboard, a variable, declared by you, to identify "source" traffic within Anura's dashboard interface. A source is where the traffic comes from.
Spam
Spam
Spam Bot
Spam Bot
These bots plague comment sections, lead forms, and email inboxes spreading unsolicited messages, advertising links, and other forms of spam. Spambots are also programmed to phish for personal information that visitors submit through forms, such as phone numbers, email addresses, and passwords.
Spamming
Spamming
Sending unsolicited emails, messages, or posts containing affiliate links.
Spider
Spider
These are automated entities that crawl the web for various reasons, such as indexing content for search engines. While they serve legitimate purposes, their visits shouldn't be counted as genuine user interactions with advertisements.
Spoofing
Spoofing
Spoofing involves disguising oneself as a known and trusted visitor. Common methods include spoofing of IP addresses, User-Agents, and Devices as well as masking DNS server origins. To combat such malicious activities, Anura utilizes multiple data points to accurately identify spoofed information, providing a robust defense against even the most sophisticated spoofing attacks and user manipulation.
Spy Bot
Spy Bot
Fraudsters use spy bots mainly for surveillance and data collection purposes. Spy bots steal personal information about a company, website, or person by logging keystrokes or intercepting packets. Some fraudsters sell that data to outside parties such as a competitor of a marketing firm for a profit.
Stickiness
Stickiness
Anura helps create customer stickiness. Stickiness occurs when new, desired features offered to clients entices them to use your product or service service more often. This helps current customers "stick" with your product or service, creating customer retention.
Stop Bots
Stop Bots
This refers to measures taken to identify and prevent automated bot traffic from interacting with digital platforms. This typically involves using software that detects bots based on environment, device attributes, and other indicators, blocking them to protect data accuracy, secure user interactions, and prevent fraud. Bot-stopping efforts safeguard websites from issues like click fraud, credential theft, and resource overload by maintaining a bot-free environment.
Structured Data
Structured Data
Structured data in digital marketing refers to any data that is organized and formatted in such a way that it is easily understandable by machines. In the context of digital marketing, structured data usually refers to the information that you can add to your website to make it easier for search engines to understand the content of your pages.
Search engines like Google use structured data to better understand the content of your page and to create rich snippets in the search results, which can help to improve your click-through rate. For example, if you have a recipe on your website, you can use structured data to indicate the ingredients, cooking time, calories, and other relevant information. Google can then use this information to create a rich snippet in the search results that includes a picture of the dish, the cooking time, and the number of calories.
Subscriptions
Subscriptions
Subscriptions are another common form of lead generation tool, giving visitors access to information like white papers, newsletters, or e-books in exchange for basic contact details. These kinds of forms don't require a significant amount of data, so they're a relatively easy way to collect information. However, this means that subscription sign-ups are easier to scam than other alternatives. Fraudsters enter false information and, when businesses reach out, they're confronted with an illegitimate lead.
Supply Side Platform (SSP)
Supply Side Platform (SSP)
Supply Side Platform, aka SSP, aggregates high-end traffic sources in order to monetize them through DSP’s (Demand Side Platforms)
Suspect
Suspect
Anura detected issues with the received visitor data and considers the visitor to be suspect. These issues will likely represent a risk to the client's required key performance indicators.
T
Target Audience Mismatch
Target Audience Mismatch
Target Audience Mismatch: Ad fraud can make it seem like you are reaching your target audience when in reality, your ads are being viewed by bots or people who have no interest in your product.
TCPA
TCPA
Telephone Consumer Protection Act (TCPA)
The laws surrounding telephone use may not seem that important, but in the world of lead follow-up, it's critical to play by the rules. TCPA is a federal law passed in 1991 that prohibits telemarketing calls to landlines without the prior consent of the owner. In the three decades since the Act's passage, this legislation has expanded to include mobile phone communication, including both voice and text messages.
The TCPA was passed in response to a growing concern involving privacy in the face of unsolicited calls – a good thing for consumers but not so good for business. With the passage of this act, the Federal Communications Commission was given the right to charge companies for making unsolicited texts or calls with fines ranging anywhere from $500 to $1,500 for each violation. For companies that make hundreds or even thousands of calls per day, this seemingly small amount can add up quickly.
Thoroughness
Thoroughness
A great ad fraud protection service needs to be thorough. Anura is committed to covering as many bases as possible, addressing virtually every known area of ad fraud. With a proprietary solution that works around the clock to detect all threats to advertising, our clients report that we find 200% to 300% more fraud than the competition.
Trader Bot
Trader Bot
Similar to spider bots, trader bots crawl around the web for pricing information. Online retailers like eBay and Amazon use trader bots to keep an eye on their rivals and offer competitive pricing or more detailed product information.
Traffic Acquisition Cost (TAC)
Traffic Acquisition Cost (TAC)
The monthly budget spent to drive relevant traffic to your web assets.
Traffic Arbitrage
Traffic Arbitrage
Traffic arbitrage refers to the practice of purchasing web traffic at a low cost and then redirecting it to a monetized platform or ad network that generates higher revenue. The aim is to profit from the difference between the cost of acquiring the traffic and the earnings from ads or affiliate offers. It requires managing traffic quality to ensure profitability without violating platform rules or risking penalties.
Traffic Origin
Traffic Origin
Anura analyzes a visitor's journey to discern their origin prior to visiting your web asset. Our system examines prior origin data to determine if a user came from known fraudulent sites or if they show signs of questionable origination. This approach enables Anura to identify and flag any potentially fraudulent activity effectively, providing clients with reliable assessments of visitor quality based on known malicious origin.
Transfer Bot
Transfer Bot
Sometimes called download bots, transfer bots are responsible for forced redirects. Transfer bots attach themselves to reputable websites and wait for visitors to click through. Instead of sendingvisitors to the site they requested, transfer bots redirect them to another site, usually one set up by a fraudster or hacker.
Transparency
Transparency
Trustworthy Accountability Group (TAG)
Trustworthy Accountability Group (TAG)
TAG is the leading global initiative fighting criminal activity and increasing trust in the digital advertising industry. TAG advances its mission of eliminating fraudulent traffic, facilitating the sharing of threat intelligence, and promoting brand safety by connecting industry leaders, analyzing threats, and sharing best practices worldwide.
Two-Factor Authentication (2FA)
Two-Factor Authentication (2FA)
Two-factor authentication is a security protocol that requires two distinct methods of verifying a user’s credentials, such as a password in combination with a text message and/or email containing a unique code to sign in.
Typo-Squatting
Typo-Squatting
This scam involves the use of misspelled domain names to trick users into visiting fraudulent sites, generating illegitimate traffic.
U
UA (User-Agent) Spoofing
UA (User-Agent) Spoofing
In order to hide fraudulent traffic coming from the same device, fraudsters employ technology that will make their one device look like many other devices. This is also referred to as Device Spoofing.
Undefined
Undefined
If a client does not pass a Source or Campaign to Anura, it's value will be returned as (undefined).
URL
URL
A URL, short for Universal Resource Locator, is more commonly known as a web address. It includes the protocol (ex. HTTP, FTP), the hostname (such as www), the domain name (like google.com or the IP address), and additional path information (folder/file).
Anura’s URL is 'https://www.Anura.io/ '
URL Hijacking
URL Hijacking
User Agent (UA)
User Agent (UA)
Is abbreviated as UA. This is the “agent” or software, typically a web browser, that one uses to look at websites. It is important for a website to know which web browser and version you are using as each browser may display the website differently.
User Environment
User Environment
Anura conducts a thorough investigation of a visitor's credibility by examining various factors, including the use of a Virtual Proxy Network (VPN) and other identifiable device and system components. This comprehensive approach enables Anura to identify any anomalies or inconsistencies that may suggest fraudulent activity. By leveraging this multifaceted strategy, Anura delivers a reliable assessment of visitor quality and provides clients with the assurance they need to make informed decisions.
UTM Code (Urchin Tracking Module)
UTM Code (Urchin Tracking Module)
UTM Codes are used by Google Analytics to track performance from any digital marketing campaign. UTM or Urchin Tracking Module is a snippet of code that you can add to the end of a URL to track the performance of campaigns and content. There are 5 variants of URL parameters you can track - source, medium, campaign, term, and content.
V
Vanity Metrics
Vanity Metrics
These are analytical numbers that companies use to sell the validity of a product, solution, or ideology as the data looks promising and is based, in part, on what makes logical sense, but when you look closely, really doesn’t give you the real picture. The data from vanity metrics give you a partial picture but can ultimately be misleading.
Verification Stripping
Verification Stripping
Verification stripping is a nefarious tactic that fraudsters use to block the protocol that is used to scan the visitor. This enables them to hide any signs that domain spoofing or other types of fraud is occurring (e.g. pixel stuffing, ad stacking, bot traffic). However, Anura is able to identify WHO is blocking our protocol so you can take action.
Video Ad Stacking
Video Ad Stacking
Multiple video ads are played simultaneously, but only one is visible. Advertisers are charged for all the ads even though only one is actually viewable by the visitor.
Video Marketing
Video Marketing
Video marketing is using videos to promote and market your product or service, increase engagement on your digital and social channels, educate your consumers and customers, and reach your audience with a new medium. (HubSpot)
View Bots
View Bots
Viewability
Viewability
The IAB definition defines viewability as "Greater than or equal to 50% of the pixels in the advertisement were on an in-focus browser tab on the viewable space of the browser page, and the time the pixel requirement is met was greater than or equal to one continuous second, post ad render." In essence, this means at least half of your ad is in view for a minimum of one second. Display ads are sold based on this viewability standard. Fraudsters know how to hide ads and trick the measurement companies into thinking they were in view when, in reality, they are not. It's also important to note that the definition of viewability doesn't specify who is viewing the ad. Instead of a legitimate person, it could be a bot, malware, or a human fraud farm.
Viewability Fraud
Viewability Fraud
When an ad is not viewable to the human eye, impressions are still counted. The most well-known fraudulent methods for this type of fraud are pixel stuffing and ad stacking. Fraud can also occur within mobile apps and on fake sites created by fraudsters. Due to impression fraud, advertisers are paying for exposure that never happened. Also known as impression fraud or display fraud.
Viewbotting
Viewbotting
Viewbotting is a type of ad fraud in which automated software, often referred to as view bots, artificially inflates the number of views on videos or livestreams. This creates the illusion of popularity, tricking platforms and advertisers into believing content has more real engagement than it does. While it might look harmless on the surface, viewbotting wastes ad dollars, distorts analytics, and undermines trust in digital advertising.
Visitor Firewall
Visitor Firewall
A "Visitor Firewall" in the context of digital marketing refers to a set of security measures or digital tools used to screen and manage the traffic coming to a website. It aims to protect the website from malicious traffic, such as bots or unauthorized visitors, while ensuring legitimate visitors have access to the site's content and services, enhancing both security and user experience.
VPN
VPN
A VPN or Virtual Private Network is a tool people and businesses use to relocate their connection to another network or location. Typically, VPNs on a residential scale allow people to remain anonymous while securely connecting through the VPN’s host. In most cases on a business scale, VPNs are used to connect to secure data centers where their infrastructure is hosted.
When connected to a VPN the IP address would appear as the host’s IP. Some VPN services allow for more security by not storing any logs of connections for a traceless web history.
Fraudsters use VPNs to hide while committing fraud.
W
Warning
Warning
Using Anura Script, the visitor tripped a rule or two in our system. They are not definitely good or bad so we mark them as a warning. The vast majority of the time this traffic represents real people with real conversion value. We have found that this accounts for our competitor's false positives. In instances where it's been necessary, the blocking warning has aligned our results with other system's confidence scores.
Web Crawler
Web Crawler
Web crawlers are internet bots that index the contents of websites. While web crawlers are generally used legitimately, they may also have the potential to be used by fraudsters to scrape sensitive data or otherwise harm a client's assets. In addition to ensuring visitors are not known web crawlers, Anura also checks for suspicious behavior that may indicate malicious intent from bots.
Web Real-Time Communications
Web Real-Time Communications
Web RTC is a free, open-source project that provides web browsers and mobile applications with real-time communication (RTC) via simple application programming interfaces (APIs). It allows audio and video communication to work inside web pages by allowing direct peer-to-peer communication, eliminating the need to install plugins or download native apps (as defined by Wikipedia)
Web RTC
Web RTC
Stands for Web Real-Time Communications. Click here for the full definition.
Webhooks
Webhooks
Is a method in which one application can push data in real-time to another. This allows applications to talk to each other rather than just responding to a request.
Website Traffic
Website Traffic
X
XML
XML
XML stands for eXtensible Markup Language and is similar to other markup languages such as HTML. It is typically designed to pass information from one system to another in a unified format. This allows one system the ability to continue to make changes, without the other system having to update code to keep up with changes.
Y
Z
Zombie Bot
Zombie Bot
As the name suggests, zombie bots turn computers into mindless drones, letting hackers control them remotely without visitors knowing their machine’s been compromised. A collection of zombie bots makes up a botnet. Here, infected computers work simultaneously to perform a certain task. Botnets are usually responsible for DDoS attacks.

Social Media Bot
Social Media Bot